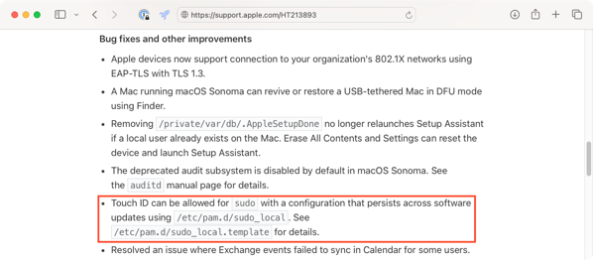
One of the requirements for getting an Apple Business Manager (ABM) instance (which also provides Automated Device Enrollment and Volume Purchase Program access) is a Data Universal Numbering System (DUNS) number, which are issued to businesses by Dun & Bradstreet (D&B). This is usually seen as an obstacle for the individual Mac admin who wants to set up an ABM instance, but it doesn’t need to be for the following reasons:
- Setting up a business does not need to cost anything in terms of money.
- Getting a DUNS number does not need to cost anything in terms of money.
- Getting an ABM instance does not cost anything in terms of money.
All three will take time and some effort, and your time always has a money value, but overall you shouldn’t get charged for anything.
Note: What I’m about to discuss applies solely to states which are part of the United States of America. If you are outside the United States, please check your own nation’s laws as what I’m about to discuss may have zero applicability to you. For more details, please see below the jump.
What makes all of this work is a business type called the sole proprietorship. For those not familiar with this type of business, it works like this:
When an individual (or married couple) starts a business, it is, by default, considered a sole proprietorship. In a sole proprietorship, the owner and the business are considered the same legal and tax-paying entity. Owners of a sole proprietorship are taxed at the applicable individual income tax rates on profits that the business makes.
Operating as a sole proprietorship in the United States (usually) requires no business formation paperwork with the state you live in. (Check your own state’s laws to verify this before proceeding.)
Because there is (usually) no paperwork or registration involved with setting up a sole proprietorship business, sole proprietorships are generally less expensive to establish and easier to maintain administratively. They also do not include any of the legal protections that other company types, like limited liability companies (LLCs), provide to separate the company’s liabilities from your personal liabilities, but this should be fine in the scenario where you’re setting up the sole proprietorship business for the sole purpose of getting a DUNS number in order to get an ABM instance.
Obtaining a DUNS number
Once you’ve decided to go this route, you will need to apply to D&B for a DUNS number and provide the following information:
- Your business name.
- Your business’s legal entity structure. (In this case, a sole proprietorship.)
- The year you started the business.
- Name(s) of the business owner(s).
- The business address, business number, and email address.
- Industry.
- The number of employees.
Note: If you are applying for a DUNS number as a sole proprietorship, your legal business name is your full legal given name (i.e. John A. Doe or Jane A. Doe). This is the name that your DUNS number will be issued to.
I would also recommend using a domain name which corresponds to the business name somehow and also getting a couple of email addresses associated with that domain for your business contact information. This may cost some money and thus invalidate the “setting up a business shouldn’t cost money” statement I made earlier, but you may also already have these.
For the business phone number, setting up a free Google Voice number or similar service should be fine; it’ll just need to be a valid way to contact you via phone.
To get started with the DUNS number application process, use the D&B link below to get started:
I recommend selecting the I have a US-based business option over the I am an Apple developer option.
![Screenshot 2023-09-04 at 3.37.25 PM.png Screenshot 2023 09 04 at 3 37 25 PM]()
The reason I recommend this is that the I have a US-based business option will start the actual process of applying for a DUNS number, while the I am an Apple developer option will only send you to Apple’s documentation on how to sign up for a DUNS number and won’t actually start the DUNS application process.
![Screenshot 2023-09-04 at 3.37.26 PM.png Screenshot 2023 09 04 at 3 37 26 PM]()
The first thing D&B will do is request you search your business name and zip code to verify that you don’t already have a DUNS number. If the search is unsuccessful (as it should be), you should see a I don’t see my business link. Click that link to proceed.
![Screenshot 2023-09-04 at 3.37.56 PM.png Screenshot 2023 09 04 at 3 37 56 PM]()
When asked to select the DUNS number package, select the free option.
![Screenshot 2023-09-04 at 3.38.09 PM.png Screenshot 2023 09 04 at 3 38 09 PM]()
When asked to set up a D&B account, set it up using the business’s contact information (email, phone number if requested, etc.) and not your personal contact information.
![Screenshot 2023-09-04 at 3.38.36 PM.png Screenshot 2023 09 04 at 3 38 36 PM]()
After that, you should be taken to the application page to request a DUNS number.
![Screenshot 2023-09-04 at 3.39.48 PM.png Screenshot 2023 09 04 at 3 39 48 PM]()
![Screenshot 2023-09-04 at 3.40.36 PM.png Screenshot 2023 09 04 at 3 40 36 PM]()
You will be requested at the end of the application to provide business verification documentation which can expedite your application, where the business’s name and mailing address are included as part of the document. As far as I can tell from my research, these documents are not required; they’re an aid to D&B to help make the verification process easier.
![Screenshot 2023-09-04 at 3.41.02 PM.png Screenshot 2023 09 04 at 3 41 02 PM]()
If you choose to provide documentation, the following are examples of acceptable documentation:
- Secretary of State Articles of Incorporation
- Secretary of State receipt of Filing
- Taxpayer Identification Number (TIN) Confirmation Letter
- Employer Identification Number (EIN) Confirmation Letter
- DBA / Assumed Name Certificate Filing
- Lease Agreement
- Mortgage
- Phone or Internet Bill
- Utility Bill
- Homeowners or Renters Insurance
- City or State Tax Permit
- Invoice from a third party
- Proof of Insurance
They must contain the legal business name and mailing address of the business. That said, if you are applying for a DUNS number as a sole proprietorship, your legal business name is your full legal given name (i.e. John A. Doe or Jane A. Doe.) Any document which has your full legal name on it would likely work for D&B’s verification process.
In my case, I decided to apply for an Employer Identification Number (EIN) for a sole proprietorship from the Internal Revenue Service (IRS) and submitted the resulting confirmation letter from the IRS as my sole supporting documentation.
If you also decide to go the same route of getting an EIN for a sole proprietorship, make sure to report when you do your taxes that you have a sole proprietorship business, that you have an EIN for it, what the EIN is, and all income you made from the business (if any). Also, please keep in mind that I am not a CPA or otherwise a licensed tax professional. I firmly recommend checking with a CPA or other licensed tax professional before applying for an EIN to make sure that what I’m saying is accurate for your situation.
Applying for an EIN for a sole proprietorship is free and information on how to do this is available via the links below:
Once you’ve completed the DUNS number application process, the next step is waiting. D&B may take up to 30 business days to process the application using the free application package and issue a DUNS number. (D&B will process the application faster, for a fee.)
Applying for an Apple Business Manager instance
Once you have received your DUNS number, you can apply for an ABM instance. Apple has instructions on how to do so available via the link below:
One thing to know about is Apple is going to request verification contact information as part of the ABM application process. Apple will call this verification contact to independently verify that your organization actually exists by talking to a real live person who can attest to it.