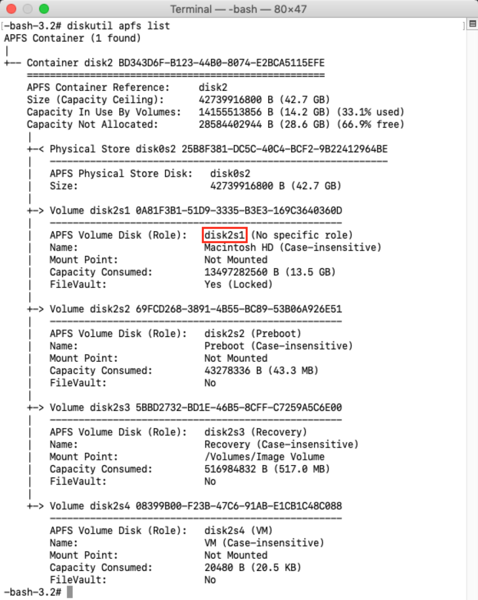
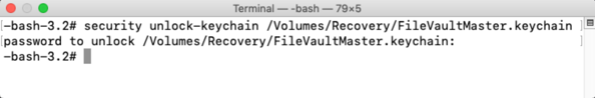
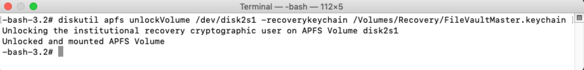
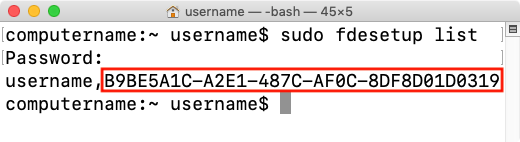
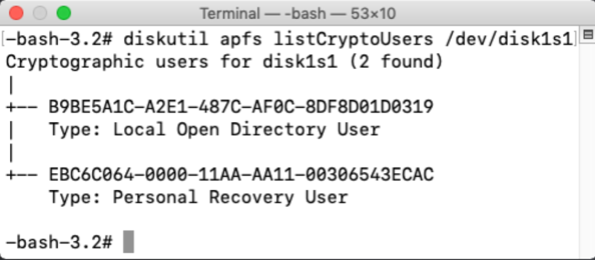
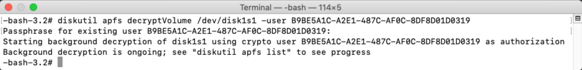
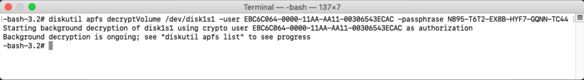
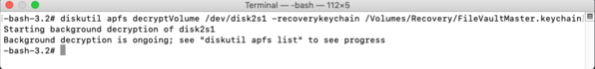
Starting with macOS High Sierra, Time Machine on Apple File System-formatted (APFS) startup drives gained the ability to create APFS snapshots. These snapshots capture the state of the startup volume at a particular point in time and can be used by Time Machine to restore files, folders or the whole startup volume. These snapshots are stored on the startup volume, but are not the same as the previous local backups that Time Machine used on Hierarchical File System Plus (HFS+) formatted drives.
On HFS+ formatted drives, Time Machine local backups are stored in an invisible directory named .MobileBackups on the root level of the startup drive.
![Figure_1_–_Location_of_the_.MobileBackups_directory_on_an_HFS+_-formatted_boot_drive.png Figure 1 Location of the MobileBackups directory on an HFS+ formatted boot drive]()
This .MobileBackups directory is mountable as /Volumes/MobileBackups and you can access the backed-up files stored inside by navigating via the command line or Finder window.
![Figure_2_–_Navigating_the_mounted_MobileBackups_volume.png Figure 2 Navigating the mounted MobileBackups volume]()
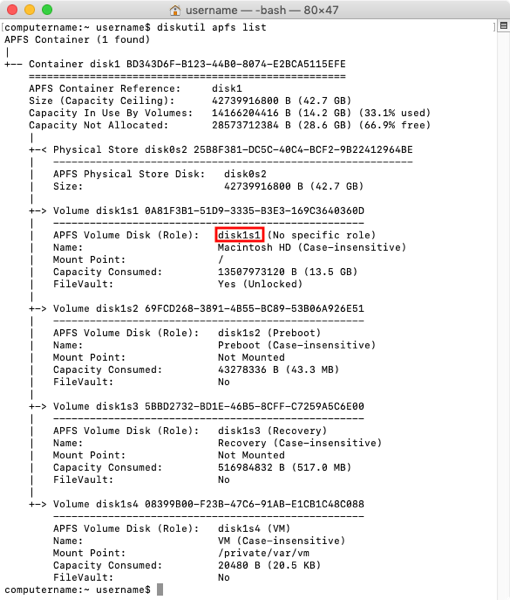
On APFS formatted drives, the /.MobileBackups directory and /Volumes/MobileBackups are no longer available. Instead, Time Machine is now using APFS snapshots to store a read-only copy of the state of your Mac’s startup drive at the time when that snapshot was taken. These snapshots are invisible to the file system, so unlike HFS+, there isn’t a directory or file location which you can access to get access to the snapshot-stored backups.
Snapshots include all files and directories stored on the startup drive at the time that the individual snapshot was made. When available, these snapshots can be used to restore the following:
- Individual files
- Individual directories
- Multiple files at once
- Multiple directories at once
- All files and directories at once
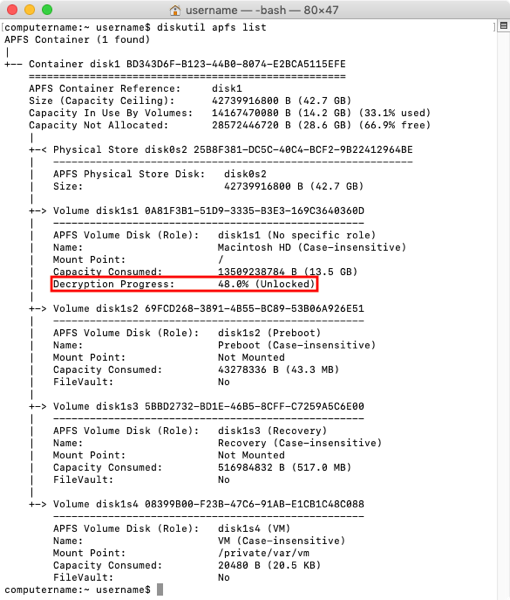
If the startup drive was encrypted at the time the snapshot was made, the snapshot will itself be encrypted. This allows the restoration of an encrypted startup drive without needing to decrypt or re-encrypt the relevant startup drive. For more details, please see below the jump.
Time Machine’s Snapshot Creation And Management
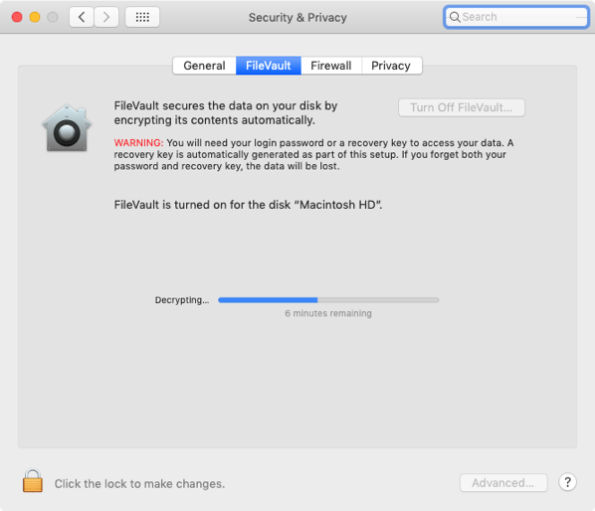
If you have Time Machine backups running on your Mac and your startup volume is APFS formatted, Time Machine will create snapshots automatically on the startup volume as part of its regular backup runs.
![Figure_3_–_Time_Machine_settings_with_description_of_snapshot_function.png Figure 3 Time Machine settings with description of snapshot function]()
If you have Time Machine backups running on your Mac and your startup volume is APFS formatted, Time Machine will be creating snapshots on the startup volume as part of its regular backup runs. The creation and deletion of these snapshots is automatically managed by Time Machine, with Time Machine monitoring the age and size of the snapshots. Time Machine has the following rules for snapshot creation and deletion:
- One snapshot of the startup volume is created approximately every hour and kept for twenty four hours.
- At least one additional snapshot of the last successful Time Machine backup of the startup volume is kept.
- One snapshot of the startup volume is created before any software update which updates macOS to a new major or minor macOS version.
If startup volume space is needed by other functions, Time Machine will use these rules when determining which snapshots to delete from the startup volume and free up the needed space.
Using tmutil To Create And Manage Snapshots
You can use the tmutil command line tool to manage snapshots created by Time Machine. tmutil can perform the following functions:
- Creating new snapshots
- Listing existing snapshots
- Deleting existing snapshots
- Thinning existing snapshots to reclaim disk space
To create a new snapshot, the following command can be run:
tmutil localsnapshot
This command will create a new snapshot and tag it with the current date and time.
![Figure_4_–_Creating_new_snapshot_using_the_tmutil_localsnapshot_command.png Figure 4 Creating new snapshot using the tmutil localsnapshot command]()
To list the new snapshot along with all other existing snapshots, tmutil’s listlocalsnapshots command will show all available snapshots stored on an APFS volume using a command similar to the one shown below.
tmutil listlocalsnapshots volume_name
For example, the following command can be run to list the available snapshots stored on the startup volume:
tmutil listlocalsnapshots /
![Figure_5_–_Listing_snapshots_stored_on_the_boot_drive_using_the_tmutil_command.png Figure 5 Listing snapshots stored on the boot drive using the tmutil command]()
To list snapshots by creation date, tmutil’s listlocalsnapshotdates command will show all available snapshots on all available APFS volumes, or all available snapshots on a specified volume.
The following command can be run to list the available snapshots’ creation dates on all available APFS volumes:
tmutil listlocalsnapshotdates
![Figure_6_–_Listing_snapshots_stored_on_all_available_APFS_volumes_using_the_tmutil_listlocalsnapshotdates_command.png Figure 6 Listing snapshots stored on all available APFS volumes using the tmutil listlocalsnapshotdates command]()
To display the creation dates of snapshots on a specified APFS volume, a command similar to the one shown below can be run to list the snapshots’ creation dates on that volume:
tmutil listlocalsnapshotdates volume_name
As an example, to display the creation dates of snapshots on the startup volume, the following command can be run:
tmutil listlocalsnapshotdates /
![Figure_7_–_Listing_the_creation_dates_of_snapshots_stored_on_the_boot_volume_using_the_tmutil_listlocalsnapshotdates_command.png Figure 7 Listing the creation dates of snapshots stored on the boot volume using the tmutil listlocalsnapshotdates command]()
To delete existing snapshots, tmutil’s deletelocalsnapshots command can be used to remove snapshots stored on an APFS volume. These deletions are specified by date, using the following format:
YYYY-MM-DD-HHMMSS
Snapshots can be deleted using a command similar to the one shown below:
tmutil deletelocalsnapshots YYYY-MM-DD-HHMMSS
For example, the following command can be run to delete a snapshot with the creation date of 2019-04-23-134055:
tmutil deletelocalsnapshots 2019-04-23-134055
![Figure_8_–_Deleting_snapshots_using_the_tmutil_deletelocalsnapshots_command.png Figure 8 Deleting snapshots using the tmutil deletelocalsnapshots command]()
As an alternative to deleting snapshots, the tmutil command line tool also includes a thinlocalsnapshots function, which has the options shown below:
tmutil thinlocalsnapshots volume_name purge_amount urgency
Purge amounts are represented as bytes, so specifying 20 gigabytes of space would be represented by the following number:
21474836480.
Urgency levels are 1 through 4, with the default urgency setting being 1.
- Urgency level 4
- Most urgent – Any current backup processes are stopped and thinning is performed immediately. The largest available backup will be the first thinned, with thinning proceeding through the next largest backups.
- Urgency level 1
- Least urgent – Current backup processes will be completed before the thinning process begins. The oldest available backup will be thinned first, with thinning proceeding through the next oldest backups.
As an example, you would use the command shown below to free up 20 gigabytes of space from the snapshots stored on the startup drive at maximum urgency:
tmutil thinlocalsnapshots / 21474836480 4
![Figure_9_–_Using_the_tmutil_thinlocalsnapshots_command_to_free_20_gigabytes_of_boot_volume_space.png Figure 9 Using the tmutil thinlocalsnapshots command to free 20 gigabytes of boot volume space]()
The snapshot thinning process may take a while to run, depending on what would need to be done to free up the requested space. It may actually free up more than the requested space, but it should free up the requested space as a minimum if the stored snapshots are taking up at least that amount of drive space.
Restoring Files And Directories From Snapshots
When restoring files and directories from a snapshot, there are a couple of options. The primary option is to use Time Machine’s graphical interface to navigate the snapshot, then restore the desired files or directories.
![Figure_10_–_Navigating_snapshot_of_boot_volume_using_Time_Machine_graphical_interface.png Figure 10 Navigating snapshot of boot volume using Time Machine graphical interface]()
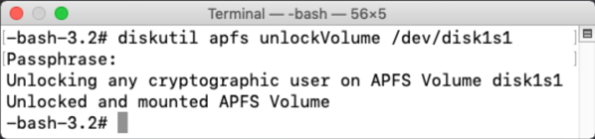
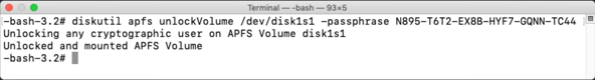
Outside of the Time Machine graphical interface, there is also the option of mounting the snapshot as a read-only volume. This action can be performed using the mount_apfs command’s -s option to mount snapshots.
![Figure_11_–_Description_of_the_snapshot_mounting_option_in_the_mount_apfs_command’s_manpage.png Figure 11 Description of the snapshot mounting option in the mount apfs command s manpage]()
To mount a Time Machine local snapshot as a read-only volume, you will need to first create a directory in a preferred location. This directory will act as the mount point for the snapshot. For this example, a directory named snapshotbackup will be created in the /tmp directory by running the following command:
mkdir /tmp/snapshotbackup
![Figure_12_–_Creating_the_snapshotbackup_directory_in_/tmp.png Figure 12 Creating the snapshotbackup directory in tmp]()
Next, we need to identify which snapshot to mount. As previously mentioned, the snapshots currently stored on the startup drive can be listed using the following tmutil command:
tmutil listlocalsnapshots /
![Figure_13_–_Listing_snapshots_stored_on_the_boot_drive_using_the_tmutil_command.png Figure 13 Listing snapshots stored on the boot drive using the tmutil command]()
For this example, the following snapshot will be used:
com.apple.TimeMachine.2019-02-23-102421
![Figure_14_–_Highlighting_specific_snapshot_chosen_for_mounting.png Figure 14 Highlighting specific snapshot chosen for mounting]()
Once the mount point and snapshot have been identified, a command similar to the one shown below should mount the snapshot:
mount_apfs -s snapshot_name backed_up_volume_name mountpoint_name
For this example, the command should look like this:
mount_apfs -s com.apple.TimeMachine.2019-02-23-102421 / /tmp/snapshotbackup
![Figure_15_–_mount_apfs_-s_command_used_to_mount_specified_snapshot.png Figure 15 mount apfs s command used to mount specified snapshot]()
The snapshot should then mount and appear as a read-only volume in the Finder.
![Figure_16_–_Snapshot_mounted_in_Finder_as_a_read-only_volume.png Figure 16 Snapshot mounted in Finder as a read only volume]()
To access the snapshot’s contents via the command line, you will need to access it via the mount point. For this example, this means the following directory path:
/tmp/snapshotbackup
![Figure_17_–_Accessing_mounted_snapshot_using_the_/tmp/snapshotbackup_mount_point.png Figure 17 Accessing mounted snapshot using the tmp snapshotbackup mount point]()
Once finished with the snapshot, it can be unmounted via the command line or the Finder.
![Figure_18_–_Unmounting_snapshot_using_the_Finder.png Figure 18 Unmounting snapshot using the Finder]()
To unmount via the command line, a command similar to the one shown below should unmount the snapshot:
diskutil unmount mountpoint_name
For our example, the following command will unmount the snapshot:
diskutil unmount /tmp/snapshotbackup
![Figure_19_–_Unmounting_snapshot_using_the_diskutil_unmount_command.png Figure 19 Unmounting snapshot using the diskutil unmount command]()
Performing Full System Restores From Snapshots
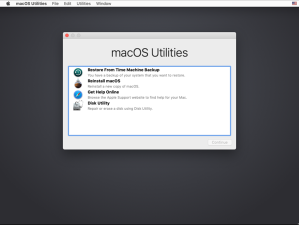
In addition to file and directory restores, Time Machine can perform full system restores from snapshots of startup volumes. These full system restores are run from the Recovery environment, using the following procedure.
First, the Mac must be booted to the Recovery environment. This can be from the Recovery volume on the Mac or Apple’s Internet Recovery. Once there, select the Restore from Time Machine Backup option.
![Figure_20_–_Accessing_the_Restore_from_Time_Machine_Backup_option_in_macOS_Recovery.png Figure 20 Accessing the Restore from Time Machine Backup option in macOS Recovery]()
Once the Restore from Time Machine assistant launches, click Continue to select the startup drive with the snapshot you need to restore from.
![Figure_21_–_Running_the_Restore_from_Time_Machine_assistant.png Figure 21 Running the Restore from Time Machine assistant]()
![Figure_22_–_Selecting_the_drive_with_the_needed_snapshot.png Figure 22 Selecting the drive with the needed snapshot]()
Once the desired snapshot is selected, the prompts can be followed to restore the snapshot.
![Figure_23_–_Selecting_the_desired_snapshot.png Figure 23 Selecting the desired snapshot]()
As part of the restore process, the startup drive is erased and the contents of the snapshot copied to the newly-erased drive.
![Figure_24_–_Confirming_the_erasure_of_the_boot_drive_and_restoration_of_the_snapshot.png Figure 24 Confirming the erasure of the boot drive and restoration of the snapshot]()
![Figure_25_–_Restoring_the_snapshot’s_contents_to_the_boot_drive.png Figure 25 Restoring the snapshot s contents to the boot drive]()
Once the restore process is completed, the Mac is automatically restarted.
![Figure_26_–_Automated_restart_of_the_Mac_following_a_successful_snapshot_restore.png Figure 26 Automated restart of the Mac following a successful snapshot restore]()
Following the restart, the Mac’s startup drive will be back to the state it was in as of the snapshot’s creation.
![Figure_27_–_Mac_at_the_login_window_after_being_restored_from_a_snapshot.png Figure 27 Mac at the login window after being restored from a snapshot]()
If the Mac’s startup drive is encrypted, the snapshots taken of the Mac’s startup drive will also be encrypted. To unlock the encryption protecting the snapshots, two additional steps must be taken as part of the restore process.
First, if an encrypted drive is selected as the restore source, the Continue button is replaced with an Unlock… button.
![Figure_28_–_Selecting_an_encrypted_drive_as_the_restore_source.png Figure 28 Selecting an encrypted drive as the restore source]()
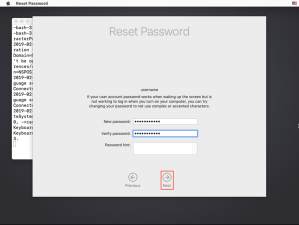
Once the Unlock… button is clicked, a password prompt will be displayed. This password can be the password of any of the FileVault-enabled accounts on this Mac.
An important thing to know is that only FileVault-enabled accounts’ passwords will be accepted by the password prompt. Personal recovery keys or institutional recovery keys cannot be used to unlock a restore source.
![Figure_29_–_Entering_a_FileVault-enabled_account’s_password_to_unlock_the_restore_source.png Figure 29 Entering a FileVault enabled account s password to unlock the restore source]()
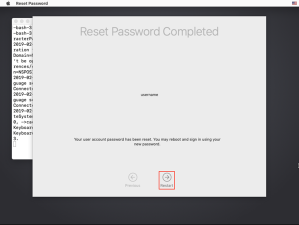
After providing the password, the Unlock… button will change to the Continue button. This will allow you to select the unlocked drive and proceed with the restore process.
![Figure_30_–_Selecting_the_unlocked_drive_with_the_needed_snapshot.png Figure 30 Selecting the unlocked drive with the needed snapshot]()
The other additional step will be at the Restoring window, where a password prompt will be displayed prior to erasing the drive. This password can be the password of any of the FileVault-enabled accounts on this Mac. This step authorizes the snapshot to be unlocked and restore its contents to the startup drive.
![Figure_31_–_Entering_a_FileVault-enabled_account’s_password_to_enable_the_restore_process_to_proceed.png Figure 31 Entering a FileVault enabled account s password to enable the restore process to proceed]()
If restoring an encrypted drive from a snapshot, the restore process will also include restoring the encryption state. This capability helps ensure the security of the encrypted startup drive is maintained. It also may save time because the drive does not have to be decrypted or re-encrypted.
![Figure_32_–_Mac_at_the_FileVault_pre-boot_login_screen_after_restoration_from_an_encrypted_snapshot.png Figure 32 Mac at the FileVault pre boot login screen after restoration from an encrypted snapshot]()