In 2018, vulnerabilities were publicly disclosed in computer processor architecture which affected the vast majority of desktops, laptops, mobile devices and servers. These vulnerabilities are referred to as Meltdown and Spectre. There is a lot of information available online about these vulnerabilities, but the cartoon below provides a decent summary of the issue:
On May 14th, 2019, additional Spectre vulnerabilities were disclosed using the name Microarchitectural Data Sampling (MDS). These vulnerabilities apply to desktop and laptop computers which use Intel processors. These processors are used by all modern Macs, but not by iOS or Apple Watch devices. These devices do not use Intel processors and instead use Apple’s own processors. For an excellent round-up of information on this developing issue, please see @zoocoup‘s post available via the link below:
https://mrmacintosh.com/mds-vulnerabilities-summary-for-macadmins-by-jason-broccardo
How to remediate this problem? For the details, please see below the jump.
There are two ways to remediate this issue, with varying levels of performance impact:
- Update to macOS 10.14.5 and later: Little to no performance impact
- Disable hyper-threading processing support: Medium to high performance impact
Mitigation with little to no performance impact
Apple and other vendors have provided a way to help guard against exploitation of these vulnerabilities via JavaScript or website-hosted malware by updating web browsers.
- Apple: Updated Safari 12.1.1 as part of the macOS 10.14.5 update
- Google: Will disable hyperthreading as part of Chrome 75 (expected release on or around June 4th, 2019)
- Mozilla: Will apply Apple’s recommended mitigation as part of Firefox 67 and Firefox Extended Support Release 60.7 (expected release on May 21st, 2019)
Mitigation with medium to high performance impact
Apple has included the option to enable full mitigation as part of the following updates:
macOS Mojave 10.14.5
Security Update 2019-003 High Sierra
Security Update 2019-003 Sierra
Full mitigation involves the following:
- Booting to macOS Recovery
- Running commands to disable hyper-threading processing
Once hyper-threading processing is disabled, the Mac will have full protection from the identified MDS vulnerabilities. Please see below for the procedure:
1. Boot to macOS Recovery

2. Open Terminal.

3. Enter the following command and press Return:
nvram boot-args="cwae=2"

4. Enter the following command and press Return:
nvram SMTDisable=%01

5. Run the following command and press Return:
nvram -xp

6. Verify the following values show up:

7. Restart the Mac.
Once the Mac has been restarted, the hyper-threading processing support will be disabled. To verify this, use the following procedure:
1. Under the Apple menu, select About this Mac

2. Click the System Report button.

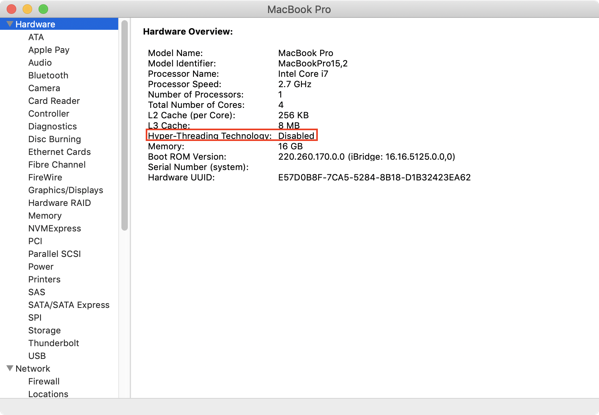
3. Select Hardware.

4. Check to see if Hyper-Threading Technology is listed as Enabled or Disabled
Enabled: Hyper-threading processing support is enabled

Disabled: Hyper-threading processing support is disabled
This status can also be checked using the command below:
/usr/sbin/system_profiler SPHardwareDataType | /usr/bin/awk '/Hyper-Threading Technology: / { print $3 }'
You can re-enable hyper-threading processing support by resetting NVRAM. For more information on how to reset NVRAM, please see the Apple KBase article linked below:
https://support.apple.com/HT204063
For more information about MDS and Apple’s steps to mitigate it, please see the Apple KBase articles linked below:
About the security content of macOS Mojave 10.14.5, Security Update 2019-003 High Sierra, Security Update 2019-003 Sierra: https://support.apple.com/HT210119
About the security content of Safari 12.1.1: https://support.apple.com/HT210123
Additional mitigations for speculative execution vulnerabilities in Intel CPUs: https://support.apple.com/HT210107
How to enable full mitigation for Microarchitectural Data Sampling (MDS) vulnerabilities: https://support.apple.com/HT210108
Note: The following Mac models may receive the right security updates, but aren’t able to support the fixes and mitigation. The reason is that Intel has not provided microcode updates for these models:
- MacBook (13-inch, Late 2009)
- MacBook (13-inch, Mid 2010)
- MacBook Air (13-inch, Late 2010)
- MacBook Air (11-inch, Late 2010)
- MacBook Pro (17-inch, Mid 2010)
- MacBook Pro (15-inch, Mid 2010)
- MacBook Pro (13-inch, Mid 2010)
- iMac (21.5-inch, Late 2009)
- iMac (27-inch, Late 2009)
- iMac (21.5-inch, Mid 2010)
- iMac (27-inch, Mid 2010)
- Mac mini (Mid 2010)
- Mac Pro (Late 2010)
