Apple has made changes as of macOS 10.13.2 to the way you can turn off APFS encryption when using the diskutil apfs decryptVolume command.
On macOS 10.13.0 and 10.13.1, an APFS encrypted volume could be decrypted using the following procedure:
- Identify the relevant encrypted APFS volume
- Unlock the encrypted APFS volume
- Decrypt the encrypted APFS volume
Once the drive has been unlocked, you could then decrypt the APFS volume using the command shown below:
diskutil apfs decryptVolume /dev/apfs_volume_id_here
As long as you were using root or admin privileges to run the command, no additional authentication was required to decrypt an unlocked encrypted volume.

However, the diskutil apfs decryptVolume command has been updated on macOS 10.13.2 to require additional authentication:
In order to decrypt using a user account’s password or personal recovery key (PRK), it is necessary to specify the following:
- The relevant user UUID
- The relevant account password or the PRK.
Note: As of macOS 10.13.2, it is not possible to decrypt an encrypted APFS volume using an institutional recovery key (IRK). You can unlock an encrypted APFS volume using an IRK, but diskutil apfs decryptVolume does not include functionality for using an IRK to authenticate the decryption of an encrypted APFS volume.
For more details, please see below the jump.
If you are planning to use a user account’s password to decrypt, you will first need to correctly identify the relevant encrypted APFS volume and which UUID you want to use.
In this case, we’ll be using the following APFS volume identifier:
/dev/disk1s1

The other assumption is that the encrypted APFS volume has been unlocked and is ready for decryption.
If you are booted from the encrypted drive, you can get the UUID of a user account by running the command shown below and matching which UUID belongs to the account you want to use.
fdesetup list

If you are not booted from the encrypted drive, there is another way to get the UUID by running the command shown below and looking at the entries listed as Local Open Directory User. However, this method will not display the account name and may require some guesswork if there is more than one FileVault enabled account enabled.
diskutil apfs listcryptousers /dev/apfs_volume_id_goes_here
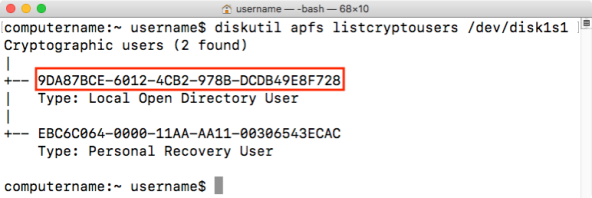
Once you have access to the UUID and password of one of the enabled accounts on the encrypted APFS volume, you can unlock using the command below. You will be prompted to provide the password:
diskutil apfs decryptVolume /dev/apfs_volume_id_goes_here -user uuid_goes_here

If you want to use the PRK, the PRK has its own UUID which only appears if you run the following command:
diskutil apfs listcryptousers /dev/apfs_volume_id_goes_here
In this case, use the UUID associated with the Personal Recovery User entry.

If you have access to the PRK associated with the encrypted APFS volume, you can decrypt using the command below. You will need to provide the relevant UUID and the alphanumeric personal recovery key as part of the command.
diskutil apfs decryptVolume /dev/apfs_volume_id_goes_here -user uuid_goes_here -passphrase personal_recovery_key_goes_here

To show the process of decrypting an unlocked encrypted APFS volume while using a personal recovery key, please see below for a video: