It can be difficult to provide consistent access for Mac admins when using a local admin account on FileVault 2-encrypted Macs, due to the way password changes are handled for FileVault 2-enabled accounts. The reason for the difficulty is that FileVault 2’s encryption doesn’t care about passwords, it only cares about encryption keys.
When an account on a particular Mac is enabled for FileVault 2, the account’s password is used to generate an key which can be used to unlock the encrypted Core Storage volume that FileVault 2 sets up on the Mac. When the password for the enabled account gets changed, the password and its associated key are updated by first requesting the previous password (and its associated key) to authenticate the change to the new password and associated key.
Assuming that the old password is provided as part of the password change process, no problem. However, if the old password is not provided as part of the password change process, the new password does not get an associated key to unlock FileVault 2 because the old password’s key was not invoked to authorize the change to a new key. The result of this is that the new password can be used to log into the OS and provide whatever password authorization duties are needed for the OS, but you still need the account’s old password to log into the Mac at the FileVault 2 login screen.
The usual fix for this situation is to run the following commands with root privileges:
1. Remove the user from the list of FileVault 2-enabled accounts
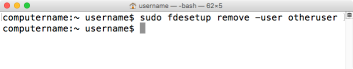
fdesetup remove -user username_goes_here
2. Add the user back to the list of FileVault 2-enabled accounts
fdesetup add -usertoadd username_goes_here

When the account is re-enabled using the fdesetup add -usertoadd command, a new key is set up for the user and the passwords are back in sync. However, there are two drawbacks to this approach if a Mac admin wants to automate this:
- You need to provide the password in a non-encrypted format of the account being enabled.
- You need to provide in a non-encrypted format either a recovery key or the password of another FV 2-enabled account on the Mac.
In short, the passwords and/or recovery key used to remove and re-enable the account in question need to be provided “in the clear”, where anyone successfully intercepting the passwords will be able to read them.
Fortunately, for those Mac admins who have a way to capture and escrow FileVault 2 personal recovery keys, there is an alternative to enabling the local admin account. For more details, see below the jump.
This approach relies on the encrypted Mac using an alphanumeric personal recovery key and the Mac admin having access to that personal recovery key.

If both of those conditions are true, see below for a way to log into a local admin account without needing to have that account enabled for FileVault 2.
1. If needed, boot up the Mac.
2. Once the Mac has booted to the FileVault 2 login screen, select an account if needed.
3. When prompted for the account password, click the question mark icon.

4. The next prompt will offer an option to reset the password using the recovery key. To access that, click the arrow icon.

5. Enter the alphanumeric personal recovery key and hit the Return key on the keyboard.

6. The FileVault 2-encrypted boot drive will unlock and boot to the OS login window.
7. At the OS login window, a Reset Password window will appear. Click the Cancel button to halt the password reset process.

8. Log into the Mac using the desired local admin account.


Note: Once a personal recovery key is used to log into a Mac, I recommend replacing it by rotating to a new personal recovery key. For those interested in automating this, my colleague John Kitzmiller has documented how to set up an automated recovery key rotation process using Casper. His post is available via the link below: